Ways to Safeguard Your Cryptocurrency Wallet
In the crypto world, wallets are like a safety locker which help you store your crypto funds safely by giving you the responsibility of managing them correctly.
If you fail to manage them correctly, then you can lose your hard-earned money.
So to manage crypto wallet properly, you’ll need to follow some step on this post.
Double Check Address.
First and simple mistake is providing a wrong public address while making any transaction.
You know that crypto addresses are lengthy and hard to remember, if you mention a digit wrong, then your money goes to the wrong address. And to make this scenario even worse, the transactions are not reversible in cryptos, so you’ll end up losing your holdings.
That’s why the first step is to make a sure wallet address mentioned correctly.
Use a Legit Website.
Today hackers can easily create a clone website of the legit website by aiming to steal the legit website users money.
For example, just look at the below image of world No1 crypto exchange Binance’s clone site, and I’ll bet you that with a bear eye you didn’t tell the difference between legit or clone until look closely on the name of website having little dots under the letter.
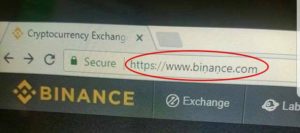
To tackle the problem first make a sure website using HTTPS connection with a valid certificate also you can use Cryptonite extension available for Chrome and Firefox that can highlight fake URLs.
Not Use Public Wi-Fi.
Not use any public wifi, especially a device that has a wallet on it.
Hackers can create a fake public Wi-Fi spot to perform the Man in the Middle attacks these types of attacks can steal your wallet information next time think before using any public Wi-Fi.
Not Install any Untrusted Software or Application.
Not only websites or wifi now hackers are creating fake crypto-related applications to steal the funds.
As smartphones are booming now especially android ones that are vulnerable to many hacking attacks, hackers move their attention on mobile users.
Now, most of the hacking attacks concentrated on the mobile user and these types of attacks done by convincing the user to install an untrusted app by tempting them in the name of exciting offers like earn free money by downloading the app or creating fake wallet app etc.
So make sure before installing any app that app is from the trusted source like Google Play Store or Apple Store.
Also, you can look at the list of Best Crypto Android Apps if you’re Android user.
Use Legit Browser Extensions.
Browser extensions enhance your browsing experience.
But some browser extensions claim that they’ll improve your experience on trading sites by giving better understandings of data; however, they track what you type, surf, and what you click on browser beside of giving you good trading experience.
These kinds of suspicious background activities of the extension could end up exposing your wallet details.
Stay Away From Phishing E-mails.
Today E-mail providers automatically detect the spammy or dummy E-mails and put them into the spam folder.
But sometimes a legit-looking E-mails appears on inbox awakening your greediness by offering big money like “Get 1000% return on investing in this crypto”.
If you open the E-mail and click on any button or link in the mail not knowing the source of E-mail is legit or not, in this scenario, your device could get compromised that may lead to your wallet.
That’s why opening up any E-mail that promising any impossible terms you should closely pay attention to spellings, and E-mail address and never click any link in an E-mail until if you know this mail is from a legit source.
Use Two Factor Authentication (2FA).
If a wallet offers a Two-Factor authentication while setting up, then, the good practice is to enable it.
Because, if the unknown person trying to gain access to your wallet at that time 2FA stop the person by asking the 2FA code set by you if the person does not give the 2FA code correctly then the person can’t be able to access your wallet.
And there are different types of 2FA one is a Google Authenticator app which uses a 6 digit code that changing minute by minute and another option is to add biometric identification like a fingerprint. Whichever you choose, 2FA is very important in order to increase security.

Turn Off Auto Update Of Your Wallet.
If you’re the one who instantly updates the wallet when any updates releases.
Then, you should consider waiting for 2-3 days after releasing any update because in initial updates application bugs can potentially create massive losses for your crypto funds so make sure the app has tested by other users before installing any updates.
Use Cold Storage.
The Best way to store the crypto fund is to store them in a Cold Storage wallets.
Cold Storage means storing the cryptos offline if a wallet stores the private key in offline its called as Cold Storage wallet.
You can use the cold storage wallet to store your crypto holdings and be kept in a secure location.
Use Good Antivirus and Anti-malware Software on your Desktop or Laptop.
If you’re relying on software wallet which installed on your desktop or mobile wallet to store the crypto funds then consider buying a premium good antivirus software is mandatory.
You already know in the digital world, there are bots, trojans, malware, etc., everywhere, and the crypto world is no different from it.

Have Multiple Backup Of Your Wallet.
Having multiple backups of the wallet is like a two-edged sword if your anyone backup reached the bad hand you could lose your hard-earned money.
At the same time having multiple backups also good when you lose a wallet, but remember store the backups in a secure place that only you know or a device that only you have access.
Conclusion.
Above are the very important parameters to safeguard your wallet from any threats.
Even after following the above steps, make sure that your wallet provider is giving services what promised and protecting the wallet private key safely if wallet provider storing all the wallet data in backend servers then data can be accessed simply by hacking the wallet provider servers or through insider’s hacking so make sure wallet provider not doing such suspicious activities backend.
After knowing wallet protective measures, you can also check out the post of Different Types of Crypto Scams to get a better understanding of safety measures.
If you got some valuable insight from the post, then don’t forget to share with your family and friends.
